Privacy is an important issue that has been widely debated. Since the appearance of Edward Snowden in 2013, who is a former NSA (National Security) subcontractor, this issue has been raised to the public domain. The case has polarized the public into two sides, where some consider him a hero as a whistleblower and some others consider him as a traitor.
As more and more people are concerned regarding the issue, the public are looking for ways to get their privacy back. It gains the popularity of a project called TOR (The Onion Routing) which has actually been around for a long time, even before this incident occurred.
TOR Project
Originally developed by US Naval Research Laboratory employees, mathematician Paul Syverson, computer scientists Michael G. Reed and David Goldschlag, onion routing protects American intelligence communications online with the main goal of privacy and anonymity.
The alpha version was launched on September 20, 2002 and was developed by Syverson and two computer scientists Roger Dingledine and Nic Mathewson. However, this project was only released to the public a year later.
How does TOR work?
Clients who want to use the TOR network need a browser that can use this feature. You can use the TOR browser which is specifically used for this.
The idea behind this is when a client connects to the TOR network, the client connection will be forwarded into three connected nodes or relays (entry nodes, middle nodes, and exit nodes) before arriving at the destination server. Along with the encryption that protects the client data, no nodes will know what the content of the data sent by the client or who sent the data.
To simplify, the client computer will create a virtual tunnel to the random server that is used as the entry node. This entry node will then re-create a tunnel to the second server called the middle node. Then the connection will be directed to the final gateway where this server will be the gateway to the destination server.
If so, doesn’t it mean that each relay will know what the client sent? This is where things get interesting. Data sent by the client will have multiple layers of encryption encoded with the public key of server A, B, and C.
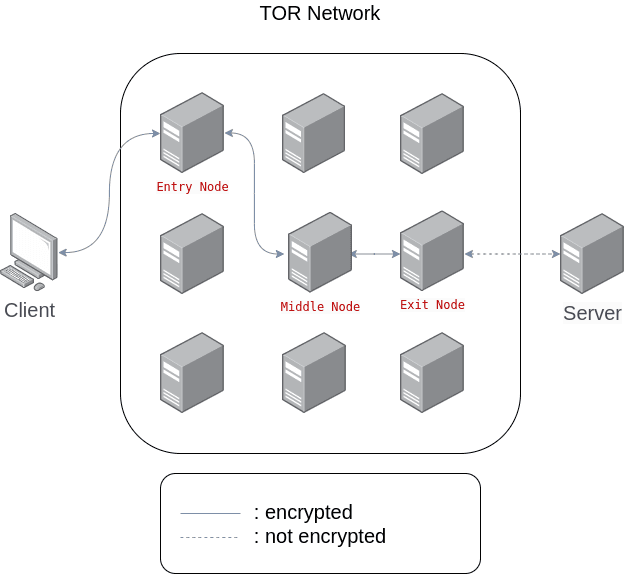
Assume that the client is connected to three random server nodes, each as an entry node (server A), middle node (server B), and exit node (server C). Data sent by the client will be encrypted using three encryptions, say that they are enc A, enc B, and enc C. These three encryptions are layered where the “outer shell” is enc A, and the “inner shell” is enc C, while enc B is between the two.
When the data is sent by the client to server A, server A will only be able to do the decryption on enc A, so that there are still enc B and C. Next, after the data arrives at server B. server B will do the same thing on ENC B. At last, the only remaining encryption is enc C which will then be decrypted by server C and forwarded to the destination server.
In this way, even though server A knows that the client is sending data, server A will have no idea the actual content of the data packet because the data will still be encrypted. Conversely, server C will know the contents of the packet sent because the data has been fully decrypted, but server C will not know the origin of the packet because server C only receives it from an intermediary server (server B). The same applies when the destination server returns a response to the client’s request.
Unfortunately, the connection between client computer to server A as well as server C to the target server are prone to be sniffed by the attackers. As we can see from the diagram above, the connection between server C and target server is not encrypted, which is very easy for the attacker to see what’s going on. This is where encrypted protocols such as HTTPS can be very useful, so that the client data will still remain encrypted until it reaches the destination server.
TOR Hidden Service
In 2013, a big case occurred which involved the TOR network. An online black market called Silk Road was shut down by the FBI and its founder Ross Ulbricht was arrested. Silk Road is an online black marketplace which is part of the dark web that sells illegal products anonymously.
By utilizing the infrastructure built with this project, various other crimes are also widely spread in place of what we now know as the dark web. In addition to selling illegal substances, selling stolen credit card numbers, and money laundering and many other crimes on the dark web, giving the TOR hidden service a very bad reputation.
However, the use of the TOR network is not always about the matters mentioned above. In the name of privacy, individuals and organizations such as activists and journalists use the TOR infrastructure in order to avoid censorship imposed by their governments. Some use TOR for other rational reasons, such as protecting themselves from cyber-spying, stalking or identity theft that may be carried out by third parties. This is where privacy and anonymity become a double-edged sword.
How does the TOR hidden service work?
If you have understood the diagram above, you know that the server that the client is targeting is a server outside the TOR network. The diagram also shows that we only use the network as an intermediary to hide our identity.
TOR hidden service works in a more complicated way and the target server is inside the TOR network itself. This is different from the regular use of TOR network, the traffic created with Onion Service or hidden service never actually leaves the network. These are marked with domains that use .onion addresses.
By using the TOR hidden service, neither the client nor the origin server will know each other, but communication will still be possible. How? Take a look at the diagram below.
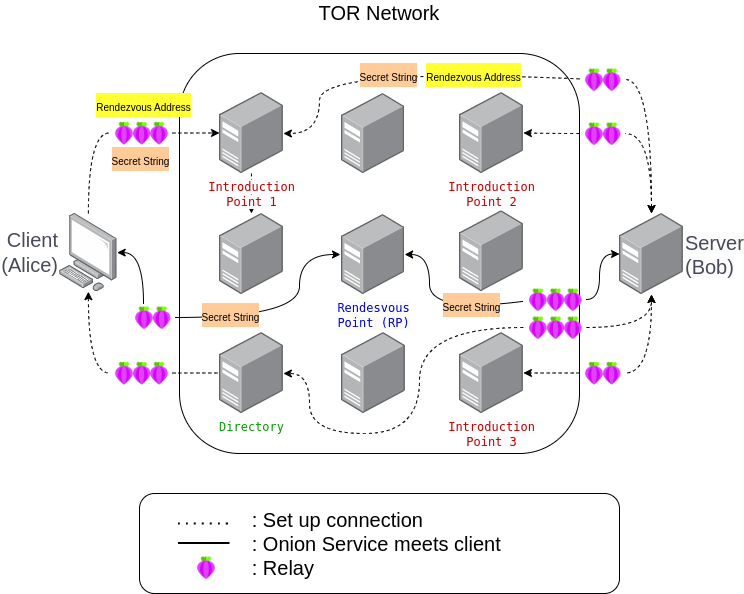
The interesting thing about the diagram above is that both the client and service will “actively” look for each other at a certain point known as Rendezvous Point. Let’s break things down from both sides.
Assume Bob is going to set up a hidden service with anonymity in mind, while Alice is the one looking for the hidden service published by Bob. Just for your information, a hidden service and an Onion Service are the same thing, so it can be used interchangeably, so you don’t get confused by both terms.
Servers (Bob)
Bob wants to create a hidden service with the .onion address. By using the Onion Service, it will randomly select three relay servers as Introduction Points (IP). To do so, Bob will go through two relays as an intermediate and use the third one as an Introduction Point.
So that the client can find the hidden service created by Bob, Onion Service will create a descriptor. The descriptor will contain information related to hidden services that have been created by Bob. This descriptor contains Bob’s public key along with the Onion Service address. Onion service then signs the descriptor using Onion service’s identity private key.
The onion service will then upload the descriptor to the Distributed Hash Table (DHT) so that the clients can get it if they want to reach this onion address. The DHT is stored on a separate server from Introduction Points (IPs) which is called the hidden service directory. Again, the TOR circuit will be used in order to upload the file anonymously.
Client (Alice)
Say that Alice wants to visit Bob’s hidden service that she knows from a public website. In this case, Alice will have no idea who the owner of this onion address is. Using TOR Browser, Alice will retrieve and use the signed descriptor stored in the DHT stored in the directory server.
After Alice gets the descriptor, she will verify the descriptor using the onion service public key. Because this descriptor has previously been encrypted with the Onion Service’s private key, we can ensure that the descriptor can only be created by the Onion Service (see step 2 above), and thus safe to use.
The descriptor will also contain information related to Introduction Points which allow the client to introduce himself to the Onion Service that is being served.
At the same time, Alice will also create a circuit to a certain server randomly in the TOR network which will then be called a Rendezvous Point (RP). As part of the rendezvous procedure, the client will be asked to provide a “one-time secret” also known as a secret string.
Alice, who already has information regarding the Introduction Points server from the descriptor, will inform the secret string & rendezvous address by establishing a circuit to one of the known Introduction Points.
The Introduction Point that receives the information sent by Alice will then proceed with the secret string and the onion address for the Rendezvous Point to Bob and the Onion Service will then verify whether the request is trustworthy..
If in this case, Bob decides to accept the request from Alice, the Onion Service will connect the two of them through several circuits to reach a Rendezvous Point where both of them will send a predetermined “one-time secret”. The Rendezvous Point will then match the strings of both so that the connection can be established.
In the end, the total number of relays involved by the both to be able to communicate is 6, where Alice needs 3 hops to reach the Rendezvous Point with the third one as the Rendezvous Point, and 3 hops from the Onion Service.
Summary
Viewed from the way it works, the TOR hidden service or Onion Service has a much higher complexity compared to the previous one. This is of course done to maintain privacy and anonymity, which are the main goals of The Onion Routing (TOR).
After all, does it mean that the anonymity offered can really guarantee the safety and anonymity of its users? Not really. The attacks have really occurred targeting the Onion Service and the TOR network as whole, exploiting any vulnerabilities and flaws it may carry which will likely be covered in a later post.
