Maybe you have thought of using your home computer as a web server that can provide website services to clients around the world. Well, you can actually do this by using an application like Nginx. Fundamentally, while you are serving the website to the clients, you are using a reverse proxy. So, what is it exactly?
What is a reverse proxy?
The reverse proxy is the server that serves as a gateway to the backend servers and directs client requests there. By its definition, we know that reverse proxy works quite differently from forward proxy. If the forward proxy resides directly on after the client, the reverse proxy resides directly before the origin server.
Comparison diagram between proxy vs. reverse proxy
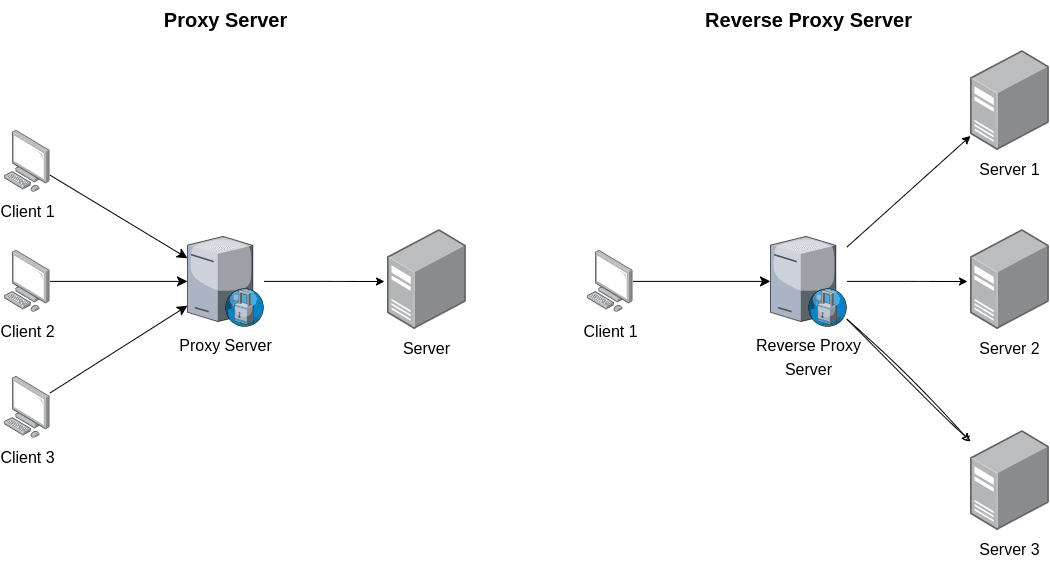
At a glance both look very similar. The difference lies in who uses it. To put simply, the proxy server is used by the clients with the main reason of obscuring their IP address. As opposed, the reverse proxy is used by the origin server with the main reason of improving the origin server security by isolating the origin server from direct contact with the client and load balancing which we are going to explain later on.
How does reverse proxy work?
When clients make a request to the origin server, the request will be directed to the reverse proxy server instead of the origin server. Just like the forward proxy, the reverse proxy has the ability to cache the content from the origin server. If requested information is available in cache and the clients are requested for it, the reverse proxy server will then send the response back to the client from the cache.
If the reverse proxy server can’t find what the client is asking for, it will then forward the requests to the origin server. Origin server will serve the information and send the response back from the origin server through the proxy.
Similar to forward proxy, the incoming and outgoing traffic will be filtered by the firewall. Additionally, reverse proxies are capable of serving multiple origin servers simultaneously, which is very helpful when dealing with massive amounts of traffic. If the reverse proxy server has its load balancing feature enabled, the proxy server will manage how the traffic should be going to a particular server based on the algorithm configured beforehand. While there are different types of load balancer based on how the algorithms work, their primary function is to distribute incoming traffic evenly across multiple servers to optimize resource utilization and avoid overloading any single server.
Load balancing algorithms
Load balancing is the process of distributing network traffic across multiple servers to improve performance, reliability, and scalability. There are several load balancing algorithms that can be used to distribute traffic among the servers. Each has its own unique approach for different use cases.
Round Robin
This algorithm handles traffic by evenly distributing the traffic across all available servers. The way it works is simple. The load balancer will send the first request to the first server in the list of available servers. If there is a new request coming in the load balancer will send the second request to the second server. This process will continue until all available servers are receiving the same amount of request and once it reaches the end of the list then it will start all over again from the beginning and the same process will continue.
Least connection
The reverse proxy server will keep track of the active connections for each available server at a time. In this way, any new incoming request will be forwarded by the reverse proxy server to the server with the least active connection, thus preventing server overloads during the period of high traffic.
Least time
This algorithm works by distributing the network traffic with the least response time. The load balancer will work by measuring the response time of each server and choosing one with the quickest response time to handle the incoming request. The server with the lowest response time is considered the most efficient and also helps to ensure users receive reliable service.
IP hashing
The clients IP addresses are hashed to determine which server will handle the request from all available servers. It ensures every request that coming from the same address will be going to the same server unless the server is unavailable. This can be useful for applications requiring session persistence.
It is likely that the reverse proxy server has the ability to distribute among the server based on the server weights. Let’s say there are 3 available servers and there are a total of 8 requests. Assuming that the first server is the most performant and the last one to be the least performant, the proxy server can be set to send requests to only for server 1 and server 2, while the server 3 serves as a backup only.
You can set the weights to server 1 to 7 and set no weight to server 2. Therefore, for every 8 requests, 7 requests will go to server 1 and 1 request will go to server 2. Server 3 won’t receive any request unless both servers are unavailable. Some methods like Round Robin and least connection may have the server weight taken into consideration.
Benefits of reverse proxy server
Because of its role, reverse proxies offer several advantages that are somewhat different from forward proxy servers.
Load Balancing
Traffic can come from anywhere around the world. Therefore, it is possible for a server to receive a lot of traffic at a time. In this situation, it is likely for the server to be overloaded, which can decrease performance and response time. Or worse, it can cause the server to go down. Addressing the issue, reverse proxy is employed to optimize traffic distribution across multiple servers to prevent this from happening.
Security
Reverse proxies generally work behind a firewall, which plays an important role in filtering incoming requests and forwarding them to the origin server. Its position, which may be separate from the origin server, may provide additional protection for the origin server, so that requests from clients will be directed to the reverse proxy server IP address. This will be very beneficial as it is more likely that the attack attempt will lead to the proxy server and not the origin server.
In a company setting, the reverse proxy will be placed in the DMZ (Demilitarized Zone) which, in general, has less strict policy than the internal network so that this server may still be accessible by the public.
SSL Encryption
As an intermediary, a proxy server can encrypt all outgoing responses and decrypt all incoming requests with the help of SSL (Secure Sockets Layer). This is extremely beneficial from a performance perspective while preserving the origin server’s resources.
Caching
Like forward proxies, reverse proxies are also capable of caching. With caching, clients can get faster response time. This will be greatly effective with the use of CDN (Content Delivery Network). With CDN, reverse proxies will be placed spread all over the world.. Thus, the clients can make requests to adjacent reverse proxies where the client is located.
In this case, every reverse proxy server that is spread throughout the world will cache the content sent by the origin server. This cache will be accessed by clients located nearby, thus improving the user experience and faster performance.
Conclusion
In conclusion, reverse proxies are servers that act as intermediaries between clients and origin servers, providing various benefits such as load balancing, security, SSL encryption, and caching. Reverse proxies can improve the performance, reliability, and scalability of web applications by distributing traffic among multiple servers, protecting the origin server from direct attacks, encrypting and decrypting data, and caching content for faster delivery. Reverse proxies are widely used in web hosting, CDN, and other scenarios where high availability and efficiency are required.
